CYBER SECURITY SERVICES
Omni Business Solutions offer a robust cyber and digital security portfolio of the industry’s leading consulting, network, cloud, mainframe, managed security, digital identity, and access and authentication services. Omni Business Solutions delivers industry-leading assessments, security strategies and resources to some of the world’s most prestigious organizations, including critical strategies such as zero trust. Omni Business Solutions security can help you quantify and understand your risks, extend your team resources, help detect and respond to threats, and unify your organization on security priorities to accelerate your business transformation.
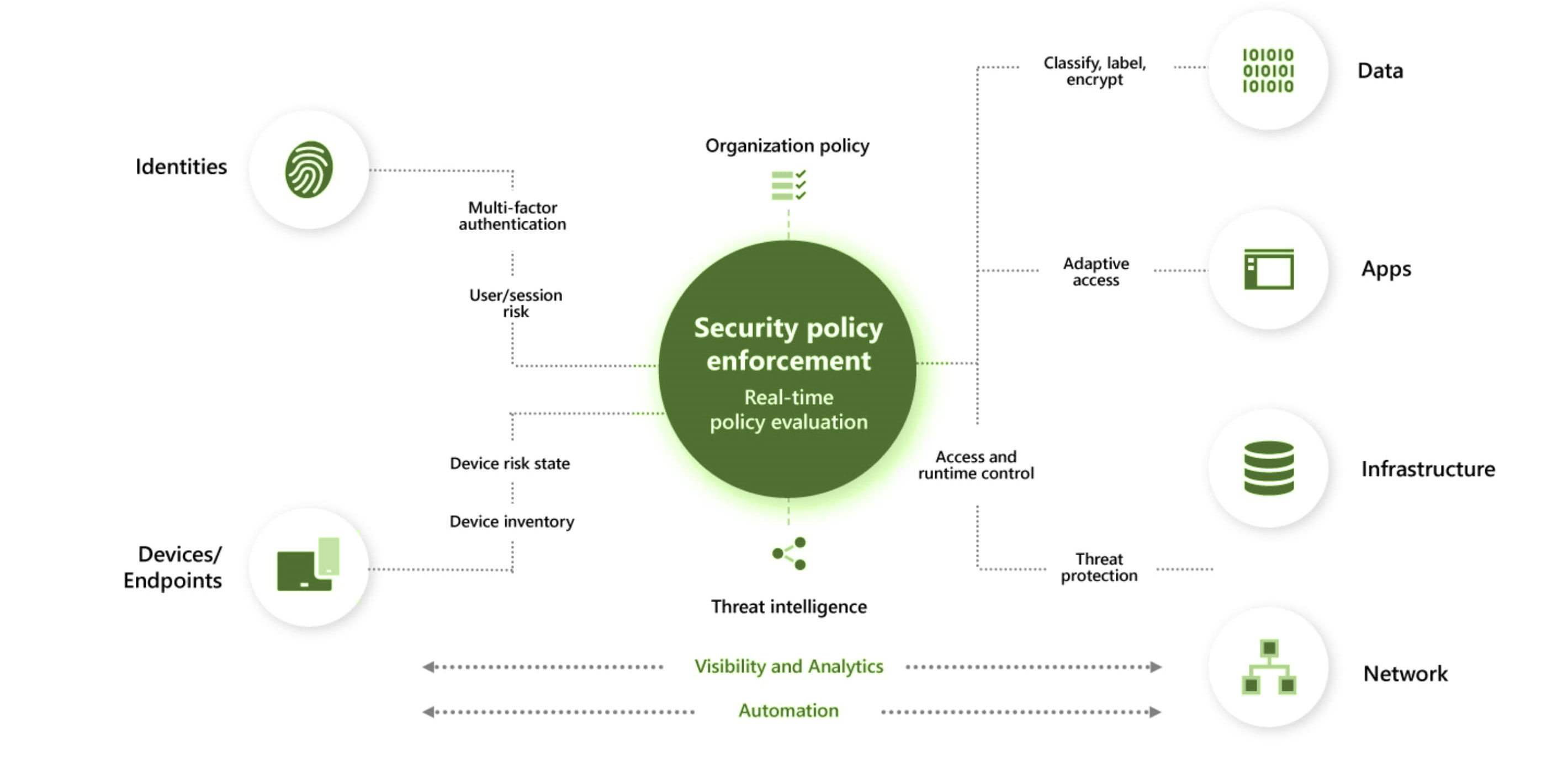
Control and defend your valuable business, data, users and assets. Deliver trust when you connect policy, analytics and controls across your entire business.













 System Trust is Zero Trust
System Trust is Zero Trust